Listen to this blog post below
Stay ahead of malicious actors by staying informed about the latest email cyber threats with this Weekly Cybersecurity News on email security.
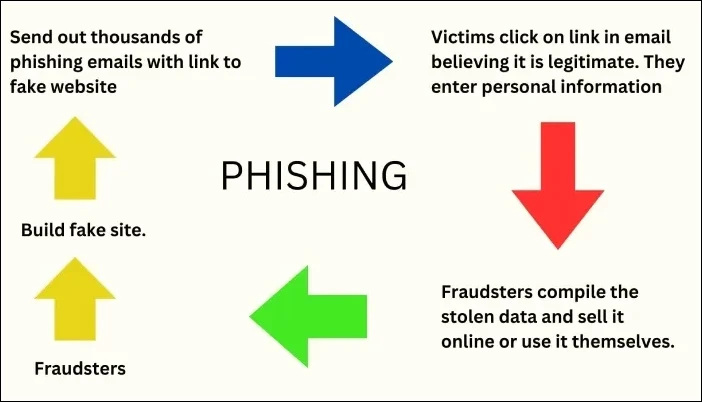
Suspected Chinese Espionage Campaign Targets US Government Emails, Breach Detected
Chinese state-sponsored malicious actors orchestrated a significant breach by infiltrating Microsoft email accounts belonging to multiple government agencies in Europe and the United States.
The breach, affecting over two dozen government agencies, underscores the ongoing cyber espionage efforts carried out by China-based threat actors. Microsoft and US national security officials confirmed the breach, emphasizing the need for collaboration between the public and private sectors to counter such threats to email security.
The breach, attributed to a malicious group called Storm-0558, targeted Microsoft-powered email accounts, including the State Department’s. Prompt action was taken to handle the threat, but evidence suggests unauthorized access to government systems since May 2023. Microsoft’s swift response, collaboration with partners, and transparency have helped address this advanced cyber attack.
The breach highlights the urgency of having robust security measures and close coordination between the public and private sectors to practice email protection.
UConn President Death Hoax Email Traced Back to Threat Actors
A malicious group, known as “SiegedSec,” has claimed responsibility for breaching the University of Connecticut’s network and orchestrating a deceptive email campaign aimed at the institution’s community.
The fraudulent email, sent early Wednesday morning, falsely announced the death of the university’s president, Radenka Maric, causing widespread alarm. In an online interview, the self-proclaimed leader of SiegedSec clarified that the breach was not politically motivated but carried out for the group’s pleasure.
The group exploited a vulnerability in the UConn Daily Digest email account, which lacked proper email security and two-factor authentication measures. This flaw allowed them to gain unauthorized access and distribute the hoax email. UConn officials, including the IT department and UConn Police, swiftly responded to the incident, removing the deceptive messages and implementing corrective measures to prevent future breaches.
The university is taking the matter seriously and conducting a thorough investigation into the breach.
Global Email Extortion: Less than 100 Scammers Behind the Menace
A recent Barracuda Networks and Columbia University study has shed light on the worldwide menace of email-based extortion scams.
In the analysis of over 300,000 extortion emails over one year, researchers focused on Bitcoin addresses utilized by scammers to identify patterns. The findings revealed that a small group of perpetrators is responsible for most of these attacks.
Approximately 3,000 unique Bitcoin addresses were observed, with the top 10 addresses accounting for about 30% of the emails and the top 100 addresses accounting for around 80%. The study suggests that fewer than 100 attackers, potentially even rarer, are likely behind these scams.
The scammers typically demand payments ranging from $400 to $5,000, with 90% seeking amounts below $2,000. This range is strategically chosen, making it more likely for victims to comply without scrutiny from their banks or tax authorities. The scammers exploit victims’ fears of embarrassing photos or videos of them, often claiming to possess compromising material obtained through non-existent spyware.
Despite the threat’s scale, the attackers’ concentrated nature offers hope for law enforcement and email security vendors to disrupt their activities and manage the threats.
Phishing Kits Empowered by Malicious npm Packages in Latest Campaigns
Researchers at ReversingLabs have uncovered a series of supply chain attacks and phishing emails involving malicious npm packages.
These packages, posing a dual threat, targeted end users and supported phishing attacks primarily aimed at Microsoft 365 users. Between May 11 and June 13, over a dozen malicious packages were discovered, imitating popular modules like ‘jquery’. Although downloaded around 1,000 times, they were swiftly removed after detection.
ReversingLabs named the campaign “Operation Brainleeches” due to its malicious infrastructure. The packages were used in phishing and software supply chain attacks, infiltrating applications and harvesting user data. The researchers stressed the importance of vigilance, urging organizations to be cautious of suspicious package characteristics, obfuscated code, and compromised open-source options.
Tracking dependencies and scrutinizing third-party code behavior is crucial for detecting potential threats and for email phishing protection against the campaign.