Keeping up with the cybersecurity world has become a need more than a necessity because of the new threats emerging every day. Not to worry! Our weekly cybersecurity news thins the herd so you can focus on what’s important and stay safe.
This week, we’ll take a look at the potential comeback of Zeppelin ransomware, apprehended threat actors, the attack on Orbit Chain blockchain, and how to keep your Google accounts and browsers the same from threat actors.
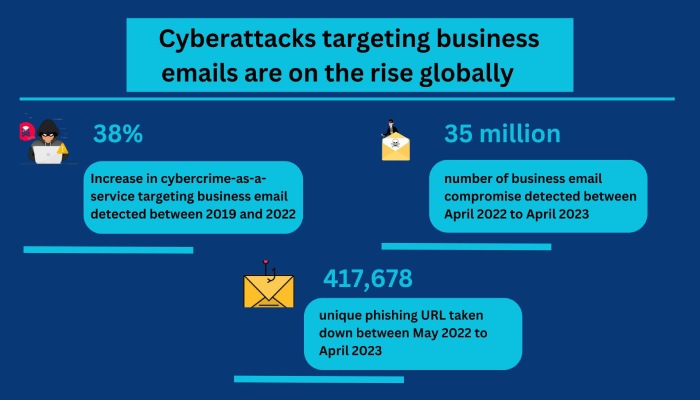
All of these news highlights underscore the importance of phishing awareness training, as well as the top-notch solutions for phishing protection, including ransomware protection and malware protection.
Source Code of Zeppelin Ransomware Auctioned for $500 on Hacking Forum
A threat actor announced that they’d sold the cracked source code of the Zeppelin ransomware for just $500.
The threat intelligence organization KELA was the first to discover the post. The authenticity of the offer couldn’t be confirmed but the screenshots are indeed real. Whoever has bought the ransomware package can use it to create a RaaS (Ransomware-as-a-Service) operation or even create a more sophisticated version for malicious use.
The person who sold it did not clarify if they were the author of the malware but added that they acquired it without a license. The threat actor did say that it was intended for a single buyer and they would freeze it until the transaction was complete. Zeppelin RaaS operation was taken down in November 2022 by law enforcement when security researchers developed a decryptor for it.
To a comment on the post, the person who sold it replied saying that this is an advanced version of the malware and does not have those same vulnerabilities.
Hacker Apprehended for Pilfering $7.5 Million from Charitable Organizations
Police have arrested a Nigerian person from Ghana. He is currently facing charges related to BEC (Business Email Compromise) attacks.
The man is Olusegun Samson Adejorin and he was arrested on 29 December 2023 – for defrauding two charitable organizations. These organizations are in Maryland and New York. The man faces multiple charges – wire fraud, unauthorized access, and aggravated identity theft. But that is not all. The US DoJ (Department of Justice) says that Adejorin accessed multiple email accounts and impersonated employees between June and August 2020.
He posed as an employee of a charity and requested a withdrawal from the other charity. He also used stolen credentials to send emails from the victim accounts to approve transactions. (Transactions over $10,000 need approvals) and was able to trick the charities. He made away with nearly $7.5 million. Adejorin now faces a penalty of 20 years for wire fraud, 5 for unauthorized access, and a mandatory 2 years for identity theft. The US DoJ may also increase it to 7 years because he registered a domain for malicious use.
You should be aware of these types of fraud and always call the organization or partner if you get any suspicious request for information change or fund withdrawal.
Last Fintech Breach of 2023: Orbit Chain Suffers $86 Million Loss
Orbit Chain experienced a security breach where the threat actors made away with nearly $86 million in various crypto coins.
The blockchain platform is not used by the investors directly and is more of an infrastructure project to support the ecosystem. It was attacked on 31 December 2023 where the threat actor used a series of drain attacks on different assets. Arkhan reports shared details and highlighted how Orbit Chain’s balance went from $115 to $29 million in an instant. The details of the vulnerability that the threat actors exploited have not been found but the threat actors are believed to be North Korean state-sponsored attackers. Orbit Chain is working with the Korean Police and KISA (Korea’s Internet and Security Agency). The nature of the attack also hints at DPRK hacking groups like Lazarus.
Meanwhile, Orbit Chain is taking the help of many international partners to track the stolen funds so they can freeze the coins.
Exploiting Google OAuth Endpoint, Malicious Software Revives Cookies to Hijack Accounts
There are multiple information-stealing malware that are abusing a Google OAuth endpoint to restore expired authentication cookies.
The endpoint has been named “MultiLogin.” Browsers have session cookies that cannot be used by threat actors as they have a limited lifespan. But this vulnerability allows threat actors to restore them after expiration, allowing them to log into user accounts. CloudSEK’s researchers shared details of the exploitation. It was revealed by a threat actor called PRISMA in October 2023.
CloudSEK’s researchers reverse-engineered it and found out that MultiLogin is intended for synchronizing accounts across multiple Google services. The request is set in the browser account for its websites such as Google Docs, YouTube, and more.
The malware extracts these tokens and account IDs from the profiles that are logged into Chrome. Then the threat actors decrypt them and regenerate expired Google Services cookies for persistent access in victim accounts.
To stay safe, we recommend that you log out of your Google account. And log back in after changing the password to ensure the key is revoked.