Best Ways to Secure Emails in 2024
Email communications are sensitive and prone to exploits, as many details and attachments are exchanged. Threat actors look for vulnerabilities in an email ecosystem and develop strategies to compromise them to steal, alter, and intercept financial details, login credentials, medical information, etc.
To prevent this from happening, you need to shrink all the email security gaps and be in charge of the overall cybersecurity. Here’s what you should focus on-
Use Strong Passwords
Weaker and easy-to-guess passwords are a big no-no, especially for your official email accounts. It’s suggested that you use an open source password manager to store and manage passwords for multiple online accounts so that you have to remember just one master password.
Use unique passwords for every account. A unique password is a combination of uppercase and lowercase letters, numbers, and special characters. It should be long and not so obvious, like your pet’s name.
Use Proxies
Conceal your location using proxies. When email traffic passes through a proxy server, the sender’s IP address is hidden and reputed through a third-party server, preventing threat actors from tracing the origin of the email.
A proxy is like a buffer between your inbox and external attackers, segregating spam and phishing emails from genuine ones. What’s better is that proxies also encrypt emails in transit and at rest so that nobody tampers with sensitive data.
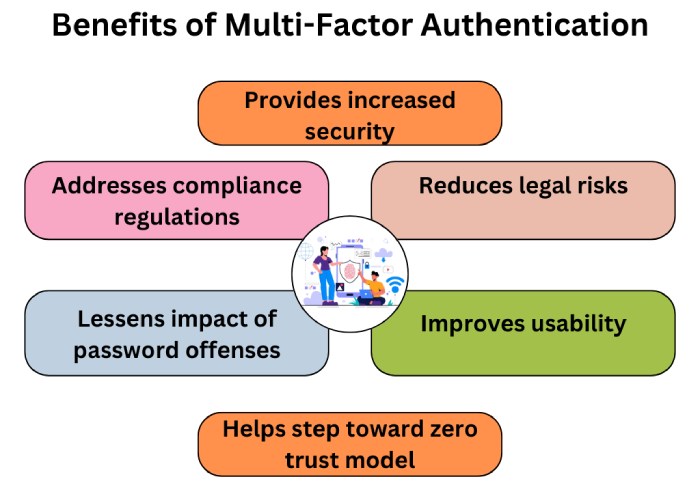
Use MFA
MFA is short for multi-factor authentication– an extra security layer that protects your email account from illegitimate and ill-intended logins. By using MFA, you minimize the probability of a cyberattack, as more than one piece of evidence is required to confirm a user’s identity. The other evidence can be OTPs, hardware tokens, fingerprints, facial and voice recognition, etc. Also, custom multi-factor authentication policies improve users’ productivity.
Use Email Authentication Protocols
Email authentication is a process of deploying protocols that check the sender’s authenticity and ensure nobody alters emails in transit. This helps prevent phishing and spoofing attempts made in your company’s name. There are three primary email authentication protocols that you can deploy in 2024-
Sender Policy Framework or SPF
To deploy SPF, you have to create an SPF record that includes all the IP addresses authorized to send emails on your behalf. Then, you publish the SPF record on your domain’s DNS so that recipients’ servers can look into it to verify whether the sending source is legitimate and authorized. If yes, emails land in the primary inboxes of recipients, otherwise, they get placed in spam folders. Sometimes, they even bounce back.
DomainKeys Identified Mail or DKIM
Upon deployment of DKIM, outgoing emails are signed digitally using a private cryptography key. Upon reception, the recipient’s server uses the public key to verify the source of the message and ensure nobody tampered with it in transit.
DKIM also prevents emails from being marked as spam since ISPs trust it to build and enhance brand reputation.
DomainBased Message Authentication, Reporting, and Conformance or DMARC
DMARC is based on SPF and DKIM. It basically instructs recipients on how to deal with unauthorized emails sent from your domain. You can choose one of the three policies—none, quarantine, or reject. The ‘none’ policy directs recipients to do nothing with unsolicited emails, while the ‘quarantine’ and ‘reject’ policies instruct recipients to mark them as spam or block them outright.
Remember that just one or two email security measures won’t suffice. You have to leave no room for threat actors and thus use multiple security elements.