Mustang Panda Exploits, White House Roadmap, Scaling Compliance Reciprocity- Cybersecurity News [September 09, 2024]
Let’s talk bout this week’s most talked-about cybersecurity news and updates, crafted to keep you updated on recent happenings. We have covered topics around cybersecurity attacks, advisories, and other relevant updates. These topics consist of the Chinese APT groups leading espionage campaigns, an initiative taken by White House to safeguard internet routing security, a suggestion to streamline compliance across global industries, Apple’s latest launches and AI-driven updates, and last but not least, Google Maps’s new feature to blur your home images online.
China’s APT “Mustang Panda” Exploits Visual Studio Code
The Mustang Panda, the China-linked APT (Advanced Persistent Threat) group, has been observed exploiting Visual Studio Code software, legitimately targeting Southeast Asian government bodies. The Chinese APT group, or threat actors, utilized the software’s embedded reverse shell functionality to invade and exploit systems by running arbitrary code and delivering malicious payloads, according to the researchers of Unit 42, Palo Alto Networks. The Mustang Panda is also referred to by other aliases, including RedDelta and Camaro Dragon. This group has been active since 2012, and it primarily focuses on government and religious institutions in Europe and Asia, particularly the South China Sea region, to outspread their propaganda and ideologies in a cyber espionage program.
Another malware named ShadowPad has been simultaneously used as a backdoor, a tool used explicitly by such Chinese espionage groups. Until now, there have been no reports or evidence claiming that these two attacks were done by the same Mustang Panda group, but the researchers expect the two could either be collaborating or be separate groups utilizing shared access points. Reports suggest OpenSSH functionality was also used to execute commands, transfer files, and propagate across networks to showcase their technological prowess. This campaign underscores the issues of frequent cyber espionage attacks on Southeast Asia and the use of innovative attack vectors they employ to achieve their propaganda goals and objectives.
White House Unveils Roadmap to Safeguard Internet Routing Protocols
The White House, United States of America, released a recent report introducing a comprehensive plan to address vulnerabilities in internet routing, such as the one related to BGP (Border Gateway Protocol). One cannot deny the usage of BGP protocol for routing data across the internet, but the only challenge is that it was not designed from the security point of view in the first place. Adding to the design flaw, significant vulnerabilities have emerged that allow malicious actors to interrupt or redirect traffic, hampering critical infrastructure security and sensitive data. After closely assessing the situation, The Office of the National Cyber DIrector (ONCD) has tried to tackle this BGP security flaw by promoting the broader adoption of Resource Public Key Infrastructure (RPKI). RPKI systems help enhance BGP security through Route Origin Authorizations (ROA) and Route Origin Validation (ROV). The only problem associated with implementing the RPKI security system is that its effectiveness depends on broad implementation by all stakeholders.
Until now, we have positively seen a 70% increase in RPKI adoption, which leads us to a promising future in internet routing domain. The ONCD’s roadmap highlights necessary steps for private network operators and government agencies to improve overall BGP security. It provides clear steps and guidelines for actions for all networks, service providers, and policy initiatives to strengthen cybersecurity infrastructure. It strictly involves the utilization of FCC proposals requiring broadband providers to implement plans to mitigate BGP vulnerabilities.
Scaling Compliance Reciprocity: A Necessary Approach to
While the security regulations are crucial and significant to be established and updated dynamically, they paved the way for establishment of varied redundant frameworks sharing standard compliance requirements that often burden organizations. Each organization is subjected to obey numerous frameworks and regulations, including NIST SP 800-53, ISO 27001, and SOC 2 Type 2, to name a few. These frameworks share many common security controls, yet organizations must adhere to all of them. This could result in a significant cost overhead, slowing business operations efficiency overall. One methodology can release this overhead burden, i.e., a reciprocity mindset. According to the reciprocity mindset, frameworks can reduce the need for repeated evaluation of common goals and objectives by accepting and implementing security assessments under one framework.
There have been examples of implementing the reciprocity approach in compliance efforts. For instance, in March 2024, the U.S. Department of Defense released its Cybersecurity Reciprocity Playbook, which promotes collaborative approach towards compliance across its systems. Also, The U.S. Office of the National Cyber Director emphasized a comprehensive policy to reduce redundant compliance requirements. In addition, leveraging tools like Open Security Controls Assessment Language (OSCAL) could further reduce inefficiencies and promote continuous security assessments across multiple frameworks.
Advanced AI Features in Apple’s Latest Launch
This Monday, Apple organization introduced a launch of its latest iPhone 16, which is well-equipped with state-of-the-art tools and technologies. Why this launch is so talked about? Because of its advanced AI capabilities designed to enhance user experience and overall security posture. The proposed model is one of its kind since they have purposely introduced generative AI into their mobile systems. This new GenAI feature will allow Apple customers to generate text and images with simple, easy-to-interpret language prompts. In parallel, Apple unveiled new updates to AirPods and the Apple Watch, enhancing their features and fan base. The latest AirPods model includes a clinical-grade hearing aid feature (pending FDA approval) available in the global market (over 100 countries). The new feature in Apple Watch 10 detects sleep arena for personalized users. Additionally, the iPhone 16 introduced a “visual intelligence” feature, allowing users to obtain detailed information regarding the objects they are querying.
These significant improvements in Apple new launches and updates can significantly help safeguard cybersecurity landscape. These AI-driven capabilities of the iPhone possess the potential to enhance real-time detection of fraudulent activity. Siri’s updates offer personalized services while ensuring and respecting individuals’ data privacy rights. The visual intelligence features in iPhone 16 can help users quickly detect and identify security risk like malicious QR codes or phishing links. By leveraging AI/ML algorithms and methodologies in iPhone, offers users both enhanced functionality and stronger protection against emerging cyber threats.
Significant Google Maps Security Alert
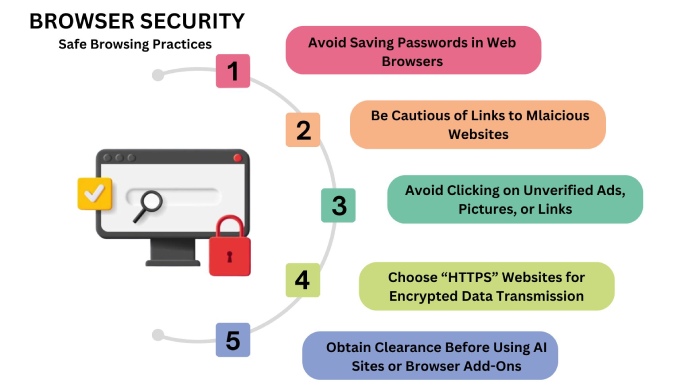
Our era is witnessing rapid increase in sextortion cases wherein a recent campaign called “Hello Pervert” used social engineering skills to intimidate and torture victims. In this attack, the malicious attackers or scammers claim to have hacked victim’s systems via malicious Pegasys spyware, including a photo of the victim’s home curated from Google Maps Street View. This attack tactic creates fear among target groups, pressuring them to clear their malicious motives. They instruct individuals to pay ransom amount to prevent any sort of embarrassing postings on internet. But to our surprise, they do not have access to any of our personal details (collected randomly from breach history). The image that they refer to is simply a home image taken from online services just like google maps. In order to safeguard oneself we must remain calm and composed and follow safe-browsing practices.
To ensure your home does not appear in Google Maps Street View, you can blur it by following these steps:
- Go to Google Maps and search for the home address.
- When Street View appears, click on the image of respective house to open the full view.
- Use the navigation tools to locate home, and then click on its image.
- Confirm the address is correct, then click the three-dot menu and select “Report.”
- Finally fill the report form and request house’s image to be blurred.
By following this 5-step process we can surely prevent scammers (malicious actors) from using images of our home and protect ourselves from these kinds of false threats in future.