Can DKIM signatures be forged?
DKIM works using encryption techniques and digital signatures that help the sender’s server transparently sign outgoing emails so that the recipient’s server can verify if the content has been altered in transit. DKIM is highly sensitive to message modifications; even the slightest difference between the content the sender sent and the recipient received causes DKIM verification to fail.
To understand how DKIM works, we first need to briefly understand what cryptographic keys are.
What are cryptographic keys?
In the context of cybersecurity, there is a method called symmetric encryption in which a user picks a password and uses it to turn a regular (plaintext) message into a scrambled (ciphertext) version. The scrambled text or encoded information can only be decoded by someone who has the same password.
There is another method called asymmetric encryption. It’s an advanced method where two keys are used instead of just one. A message is locked with one key and can only be unlocked with the second key, and vice versa. One of the keys is private (the owner keeps it secretly) and the other one is public (shared openly).
DKIM’s working style involves the use of the asymmetric encryption method.
How does DKIM work?
DKIM uses an asymmetric encryption method to sign all the emails sent from your domain. This helps confirm that no malicious entity has tampered with the email content in transit. If the email is altered, it’s either marked as spam or rejected, depending on the DMARC policy (quarantine or reject) set by the domain owner.
Here is a step-by-step explanation of how this all works-
Producing DKIM keys
The domain owner generates a cryptographically secured pair of public and private keys. These can be produced using OpenSSL or an online DKIM generator tool. The minimum key size recommended is 1024 bits, but even that is considered weak and breachable, so it’s better to go with 2048 bits.
Adding DKIM signature
Whenever an email is sent from your domain, the sender’s mail server signs it with a DKIM signature using the private key. Every signature has a coded summary of the metadata and email content, making it unique.
Email verification
When the recipient’s mail server receives your email, it checks the domain name and queries the DNS about the DKIM record corresponding to it. Then, it retrieves the key in the DKIM record and uses it to verify the signature.
Signature verification and authentication checks
The signature verification is done by decrypting the signature and recalculating the hash of the email’s headers and body. If the computed hash matches the decrypted signature, DKIM passes; otherwise, it fails, indicating possible tampering. The outcome affects email handling based on spam filters or DMARC policies.
Can threat actors forge DKIM signatures?
Well, DKIM signatures are designed to be cryptographically secured and, hence, are not forgeable under normal circumstances. However, there are still some potential ways through which malicious actors can abuse DKIM signatures-
Private key compromise
If a threat actor gets access to your private DKIM key, they can forge legitimate DKIM signatures. That’s why it’s recommended that you rotate the keys frequently. So, even if your key is compromised, the threat actor won’t be using it for long.
Header injection attacks
Some mail servers may allow header injections, allowing attackers to prepend malicious headers to an already-signed message. Proper mail server configurations mitigate this risk.
Canonicalization weaknesses
Attackers can exploit a poorly implemented relaxed canonicalization to manipulate email content without breaking the DKIM signature. Some implementations also have problems, such as extra spaces or line breaks, that lead to unintended interpretations. Attackers could exploit this to subtly alter email content without invalidating the DKIM signature.
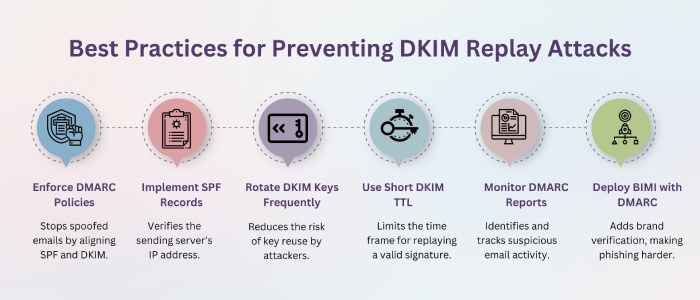
Replay attacks
Sometimes, a valid DKIM signature is forwarded and reused by a bad actor. If an email is sent using this technique, it will pass DKIM checks as this protocol is not capable of verifying the sending IP; it just checks the domain signature. To avoid this, complement DMARC with SPF and DMARC.
Final words
While it’s true that DKIM significantly improves email security by verifying message authenticity, it doesn’t offer 360-degree protection against email phishing and spoofing. If DKIM configurations are incorrect or weak, your domain will be vulnerable to exploitation. To strengthen protection, businesses should enforce strong DKIM policies, rotate keys regularly, and combine DKIM with SPF and DMARC for a layered defense.
Ultimately, email security is only as strong as its weakest link—a properly configured DKIM setup can make a huge difference in preventing fraud and protecting brand reputation.
It’s important to stay proactive about auditing your email authentication settings to ensure that cybercriminals don’t easily target your domain and brand’s reputation.