What happens to the emails that don’t pass the DKIM checks?
Let’s do a quick recap of how DKIM works so that we can go further into knowing what happens to emails that don’t pass the DKIM authentication checks.
DKIM allows a domain owner to digitally sign all the emails going out of their domain so that receiving mail servers can check if the content was altered in transit. To deploy DKIM, a pair of cryptographically secured public and private keys is generated. The public key is published on the domain’s DNS, and the domain owner stores the private key securely. When the receiving server gets the email, it retrieves the public key from the DNS and matches it with the private key used to sign the email. When both the keys match, DKIM authentication passes, and the email lands in the inbox; otherwise, it fails. But what happens to the emails that fail the DKIM checks? This blog precisely answers that only.
When DKIM fails and DMARC policy is present (combining SPF and DKIM results)
It’s advised to implement DKIM in tandem with DMARC. This is because if DKIM fails, the receiving server will take the action you instructed through your DMARC record. There are three DMARC policies, one of which you can implement in your DMARC record.
Note: Please note that DMARC works on the basis of SPF and DKIM results. If you have implemented only DKIM and DMARC for your domain, then DMARC results will only rely on DKIM authentication checks. In easier words, if you have only DKIM and DMARC in place, and an email didn’t pass the DKIM check, then it will fail the DMARC check as well.
However, if your domain is protected with SPF, DKIM, and DMARC, DMARC depends on the results of both SPF and DKIM. For an email to pass DMARC, it should pass the checks for at least one of the protocols.
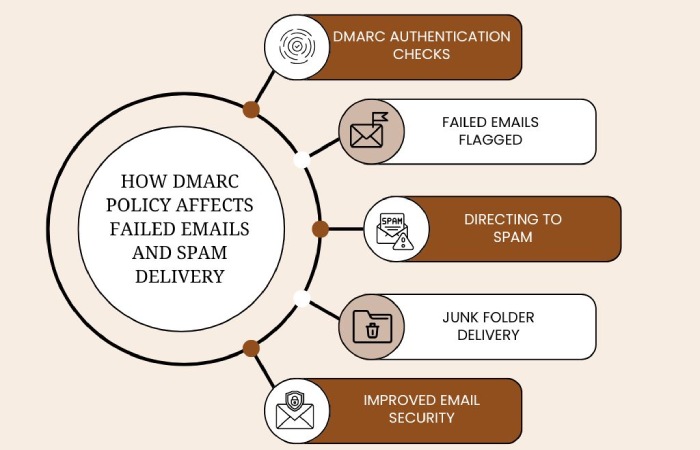
Here’s what each of the policy instructs–
p=none (None policy)
It’s called the monitoring policy, as it instructs the receiving server to take no action against emails that fail the DKIM check. Such emails are usually delivered, but reports are sent to the domain owner so that they can evaluate the details further.
p=qurantine (Quarantine policy)
Under this DMARC policy, failed emails are sent to the recipient’s spam or junk folder.
p=reject (Reject policy)
Under this DMARC policy, the email that fails the DKIM check is rejected outrightly by the receiving mailbox. The email doesn’t even land in the spam folder; it simply bounces back to the sender.
When DKIM fails but there is no DMARC in place
If DMARC is not in place, the email might still be delivered to the recipient’s inbox. Depending on the mail provider’s filtering rules, it could be marked as spam or junk. Some mail servers might reject it, but this is less common without DMARC.
What are the possible reasons for DKIM failure?
Apart from unmatched digital signatures, there are a few more reasons why DKIM protocol is triggered toward an email, even if it’s sent by a genuine person-
Expiration of the DKIM signature
This happens when an email is delayed or queued in the spam filter for a long time. In such a case, it usually gets delivered after the x= timestamp has passed. x= is the expiration timestamp; so, if the current time exceeds this value, the signature is treated as expired, and DKIM fails because of it.
To avoid this, don’t set excessively short signature lifetimes unless you are dealing with a high-security environment.
Misconfiguration in DKIM setup
Common misconfigurations in a DKIM setup include– typos in the DNS record, use of an incorrect selector, or DNS propagation delays. Sometimes, the error occurs because of using corrupted or mismatched keys. That’s why it’s recommended that you double-check DNS records using online lookup tools. Also, validate the private and public key pair with OpenSSL.
DKIM signature broken due to forwarding
Email forwarding systems and mailing lists often modify message content or headers, leading to DKIM failures. This can be prevented using ARCs or Authenticated Received Chains. What else you can do is use the ‘rua’ tag in your DMARC record to receive failure reports. If these reports are evaluated properly, they help enforce strict rejections if forwarding is common.
Final words
Being a domain owner or one of the official email senders of a domain, it’s your responsibility to ensure that you have properly configured DKIM so that your messages land in the inboxes. Failing DKIM alone doesn’t always mean rejection, but it significantly increases the risk of your email being flagged as suspicious.
Have you run into any DKIM issues with your emails, or are you looking into setting up DKIM for a domain? Whatever the case is, reach out to us or schedule a demo with DuoCircle to get started.