Dealing with DMARC failures: Here’s how you can fix the errors
DMARC is one of the most fundamental and robust email authentication protocols out there. It not only keeps impersonators at bay and protects your domain from being misused but also gives you visibility into who is sending emails on your behalf.
When your organization’s security is at stake, you have to make sure that all your security efforts are actually working together. Even a small gap or misconfiguration of an authentication protocol like DMARC can cause your emails to fail verification checks, which means they would end up in the recipient’s spam folder instead of their inbox. To add to this, there is also a risk of someone else spoofing your domain to send fake emails. This can hurt your reputation, confuse your customers, or even lead to data breaches if someone falls for a phishing email pretending to be you.
But if you’re doing everything by the book, or at least trying to do so, why are you encountering DMARC failures?
Let us take a look at why:
Why does DMARC even fail?
Here’s the truth: Implementing DMARC is a tricky game, and DMARC failures are more common than you think! So, let’s understand why DMARC fails, even when you think you’ve set everything up right.
DMARC alignment failures
One of the most common reasons DMARC fails is because of something called domain alignment. Basically, DMARC verifies whether the domain in your “From” address (what recipients see in their inbox) is the same as the Return-Path header (for SPF) and the DKIM signature header (for DKIM). Even if one of them matches your “From” domain, your email is considered legit, but if neither of them matches, DMARC fails the email—even if it is a real, legitimate message. This usually happens when you’re using third-party systems for sending emails, like email marketing platforms or customer service systems.
DKIM signatures aren’t properly configured
Another reason why DMARC might be failing for your domain is that you haven’t mentioned the DKIM signature in your DNS. In such cases, your email service provider assigns a default DKIM signature to your outgoing emails, which obviously does not match the one in the From header. This mismatch inevitably becomes a thing of concern for the receiving Mail Transfer Agent (MTA) and leads to DKIM and DMARC failure.
You missed adding sending domains to the DNS
This is one of the most common reasons why DMARC fails for most organizations. When you configure DMARC for your domain with SPF, you’re required to upload a list of all the authorized senders and addresses in your DNS. The list should include all the senders you have authorized to send emails on your behalf, so whether it is one of your subdomains or a third-party service, it should have it all!
But if you fail to add a source, you might face SPF failure issues, which means that subsequently, DMARC will also fail for that source.
Remember, even if this source is legitimate, if you do not list it in the DNS, the receiving server has no way of knowing that it’s allowed to send on your behalf. So your emails are bound to fail SPF and DMARC checks.
Your emails go through intermediary servers
When you forward an email, it does not go straight to the new recipient; it is routed through an intermediary server. These servers usually make small changes to the messages, such as adding footers or modifying headers. While these changes are not that big and are harmless, they can actually break DKIM authentication. And once your DKIM signature is broken, the receiving server can’t verify that the message really came from you. On top of that, the intermediary server that forwarded the email is probably not listed in your SPF record, so SPF fails too. When both DKIM and SPF fail, DMARC fails as well, even though the original email was completely legitimate.
How do you fix the DMARC failure error for your domain?
Now that we have identified what causes DMARC failure, let’s move on to the next steps, fixing the issues before your important emails end up in spam or get blocked entirely
Start off with a relaxed DMARC policy (p=none)
If you’re just starting out with DMARC, make sure that you begin by implementing a lenient DMARC policy, i.e., p=none. This policy does not provide you with any protection, which means it does not block any unauthenticated emails but helps you monitor and understand how your domain is being used (or misused) by generating detailed reports. Once you have a clear idea of how your emails are being sent and received by servers, you can gradually move on to stricter policies like p=quarantine and eventually to p=reject for full protection.
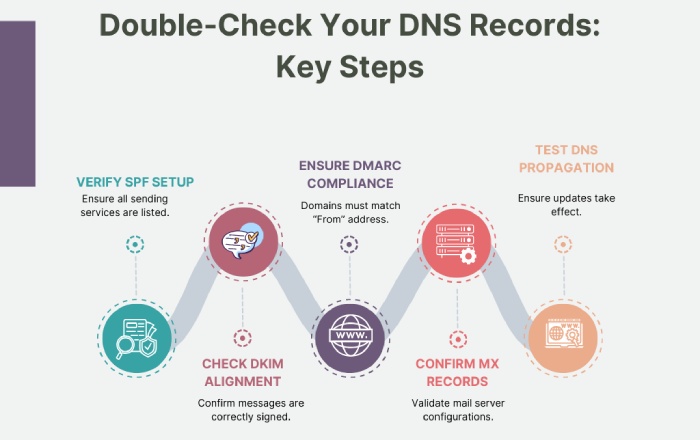
Check if SPF and DKIM are properly aligned
Make sure your SPF and DKIM records are set up correctly and align with your domain. SPF should list all services allowed to send emails for you, and DKIM should sign messages using your domain. If the domains used in SPF and DKIM don’t match your “From” address, DMARC will fail—even for valid emails. Double-check your DNS records to ensure everything lines up.
Moreover, make sure that you have both SPF and DKIM aligned for your domain. Although you need only one of them for DMARC alignment, it is always a good idea to properly align them both so that you have a stronger and more reliable setup.
Continuously monitor and fine-tune your DMARC setup
Finally, it is always a good idea to keep an eye on what’s happening with your email-sending domain. Turn on DMARC forensic reports (RUF reports) to get detailed information about emails that fail DMARC checks. These reports show you what went wrong—like which email failed and why—so you can quickly spot the problem and fix it. By checking these reports regularly, you can fine-tune your email settings, block suspicious senders, and make sure your real emails are getting delivered properly.
Need help configuring DMARC for your domain? Book a demo with DuoCircle today!