CrushFTP Exploit Alert, Lucid Phishing Surge, WordPress Plugin Exploit – Cybersecurity News [March 31, 2025]
Cyber threats are evolving, and this week has been no exception. From a dangerous CrushFTP vulnerability under active attack to a sophisticated phishing platform preying on mobile users, cyber criminals are refining their tactics. Hackers are also exploiting WordPress features to stay hidden, while a new Android malware is after crypto wallets. With attackers moving fast, staying informed is more critical than ever—here’s everything you need to know.
CrushFTP Authentication Bypass Flaw Actively Exploited in Attacks
Attackers are actively exploiting a major security vulnerability in CrushFTP file transfer software (CVE-2025-2825). Outpost24 discovered the flaw and showed how it allows remote attackers to gain unauthenticated access to unpatched CrushFTP v10 and v11 servers.
CrushFTP released patches on 21 March 2025 and warned users to update immediately, emphasizing that an exposed HTTP(S) port could allow unauthorized access. Still, attackers quickly began exploiting the flaw. A week later, security platform Shadowserver detected multiple attacks on vulnerable CrushFTP servers exposed to the internet. They also confirmed ongoing exploitation attempts, sharing that at least 1,512 vulnerable servers were still online as of 30 March. File transfer software like CrushFTP is a frequent target for ransomware groups, particularly Clop, which has previously attacked similar products like MOVEit Transfer and GoAnywhere MFT, which is why you need to be on your guard.
Make sure you update the software to the latest version immediately. Those unable to patch right away should enable the DMZ network option to reduce exposure. Organizations using file transfer tools should also monitor for signs of exploitation and ensure their cybersecurity measures are up to date.
‘Lucid’ Phishing Platform Fuels Surge in iOS and Android SMS Scams
A PhaaS (Phishing-as-a-Service) platform called Lucid has been used to target 169 entities across 88 countries, sending deceptive messages via iMessage (iOS) and RCS (Android).
Lucid is sold through a subscription-based model, allowing other attackers to access over 1,000 phishing domains, auto-generated phishing sites, and professional-grade spam tools. Security researchers at Prodaft have also found a connection between Lucid and another phishing platform called Darcula v3, which suggests a larger network of cybercriminal activity.
The messages are made to look like official notifications from government agencies, delivery services, and financial institutions and the people who click on these links are taken to fake websites that steal personal and financial information (names, addresses, and credit card details).
Knowing such attacks is half the job done because then, you just have to avoid clicking on links in messages, even if they appear to come from a trusted service. If you receive an alert about a payment or package, best visit the official website instead of using the link provided in the text.
Hackers Leveraged WordPress MU-Plugins to Conceal Malicious Code
Hackers are also exploiting the mu-plugins (Must-Use Plugins) directory in WordPress to execute malicious code on every page and avoid detection.
The method was first noticed by security researchers at Sucuri in February 2025 but is now being widely used. The mu-plugins feature is meant for essential site-wide functionality, but attackers are abusing it to maintain a hidden presence on compromised websites. They deploy three different types of malicious payloads in the mu-plugins directory. The first, redirect.php, redirects visitors (except bots and logged-in admins) to a fake browser update page that installs malware.
The second one, index.php, is a web shell backdoor that fetches and executes PHP code from a remote GitHub repository that the attackers use to execute commands on the server and steal data. The last one is custom-js-loader.php, which injects JavaScript that replaces all images with explicit content and hijacks outbound links to display shady popups.
The webshell attack is particularly dangerous because it gives attackers full control over the compromised server. That’s why WordPress site administrators should ensure that all plugins and themes are up to date and remove any that are unnecessary. Strong admin credentials and multi-factor authentication should also be used.
Phishing Service Uses DNS-over-HTTPS to Evade Detection
There’s another newly uncovered PhaaS (Phishing-as-a-Service) operation called Morphing Meerkat that has been using DNS over HTTPS (DoH) to evade detection while phishing.
It was discovered by Infoblox, who shared that it has been active since at least 2020. The platform uses a centralized SMTP infrastructure to send spam emails that are crafted to create urgency by using subject lines like “Action Required: Account Deactivation” and are sent in multiple languages, including English, Spanish, Russian, and Chinese. If a victim clicks on a malicious link, they are redirected through a series of open redirects on compromised sites, fake domains, and free hosting services. Once on the final phishing page, the kit queries Google or Cloudflare for the victim’s email provider using DoH and serves a fake login page pre-filled with their email address, ready to steal their info.
It’s best to block access to unauthorized DoH servers and restrict connections to ad tech and file-sharing platforms that are not essential to business operations. Organizations should monitor their DNS traffic closely and educate users on identifying phishing emails.
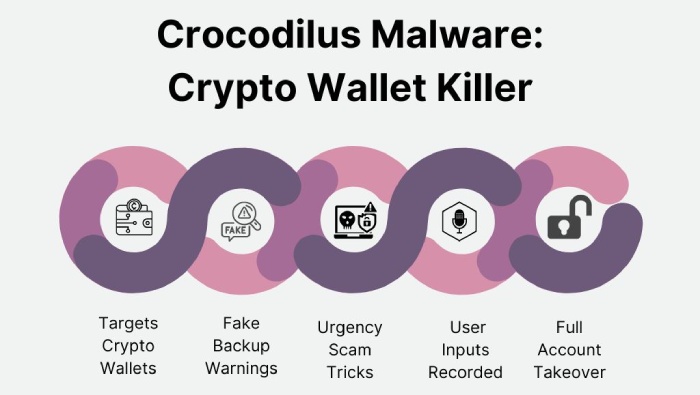
New Crocodilus Malware Targets Android Users’ Crypto Wallet Keys
There’s also news of a new Android malware called Crocodilus that is tricking cryptocurrency users into revealing their wallet seed phrases.
The malicious software deceives victims by displaying a fake warning message, urging them to back up their wallet keys within 12 hours or risk losing access. Once users follow the instructions and view their seed phrase, the malware records it, and threat actors gain complete control of the victim’s crypto wallet and drain its funds.
Crocodilus is more than just a phishing tool—it is a fully developed banking malware with remote access capabilities. It is spread using a special dropper that bypasses security features in Android 13 and, later, avoids detection by Play Protect. Once installed, the malware gives the threat actors access to Accessibility Service permissions, allowing them to monitor screens and even overlay fake login pages on banking and cryptocurrency apps to steal credentials.
You should avoid downloading apps from third-party sources or clicking on suspicious links from SMS or social media to stay safe. Keeping Play Protect active and being cautious of apps requesting Accessibility Service permissions will also help!