ClickFix Hacking Tactic, Android Credit Scams, Marks Spencer Cyberattack – Cybersecurity News [April 21, 2025]
This week, we will explore how malware disguised as security tools is stealing credit card information and how hackers are initiating customer support scams. From supermarket delays to SIM data leaks, it’s been anything but quiet on the cyber front. We will also examine Microsoft’s internal misstep, which resulted in the locking out of thousands. Here’s what you need to know before you click, tap, or swipe again.
ClickFix Tactic Used by Hackers in New Social Engineering Campaign
ClickFix attacks are becoming more common in cyber espionage. These attacks trick users into running harmful code by disguising it as a fix for fake download or login issues.
ClickFix is a social engineering technique where attackers create fake websites that look like trusted services, like document-sharing or login portals. Victims are directed to these pages through phishing emails or malicious ads and shown an error message, such as a failed download. They’re then told to click a “Fix” button, which gives them a PowerShell or command-line script to run, but this script installs malware. Between late 2024 and early 2025, several well-known groups adopted this tactic.
fcybercriminals
Kimsuky threat actors targeted researchers and think tanks by pretending to be Japanese diplomats. Victims were sent fake PDFs that led to a fake registration page and a script that installed QuasarRAT. On the other hand, MuddyWater hackers tricked Middle East-based organizations using fake Microsoft alerts to install surveillance tools. Groups like APT28 and UNK_RemoteRogue have also used similar methods, spoofing Microsoft and Google pages.
So, how do you stay safe? Never copy or run scripts from untrusted sources. Avoid clicking on links in suspicious emails, and always verify update prompts directly from the software provider.
New Android Malware Targets Credit Cards for NFC-Based Relay Scams
A new Android malware platform called SuperCard X has surfaced, enabling attackers to make small payments and ATM withdrawals using stolen credit card data. It works by tricking users into sharing their card details and installing a malicious app that reads and transmits card information via NFC. SuperCard X is a malware-as-a-service (MaaS) platform built using code similar to NFCGate and NGate, which were previously used for contactless card theft in Europe. Promoted on Telegram, SuperCard X even offers customer support to cybercriminals using the service.
Mobile security enterprise Cleafy found the malware in active use in Italy, where attackers tailored it for local use. The attack typically starts with a fake SMS or WhatsApp message that pretends to be from a bank. Victims are asked to call a number where a scammer impersonates bank staff. They’re persuaded to share card details and remove transaction limits, and then install an app called Reader, disguised as a security tool. This app accesses NFC to steal card data. Another app, Tapper, receives the data and mimics the card to make transactions.
SuperCard X avoids detection with minimal permissions and encrypted communication. Never share card details or install apps based on messages or calls claiming to be from your bank.
Marks & Spencer Hit by Cyberattack, Order Deliveries Delayed for Customers
Marks & Spencer (M&S), the major British retailer, is dealing with a cyberattack that has disrupted parts of its operations. The issue affected services like Click and Collect, though stores, the website, and the app are still up and running.
The cyberattack began a few days ago, prompting M&S to make changes to how some of its stores operate. They confirmed the incident through a press release on the London Stock Exchange and said they’re currently working with external cybersecurity experts to manage the situation. M&S has not shared exactly what kind of attack took place or whether sensitive data was accessed.
However, it has informed both the National Cyber Security Centre and data protection regulators. The organization emphasized that protecting customers and business operations was a priority. Customers using the Click and Collect service were told to wait for a confirmation email before visiting stores, as delays have occurred.
So far, no threat actors have claimed responsibility for the attack but M&S has sent out emails to affected users, apologizing and promising to restore normal services soon. If you’re a customer, watch out for the notification and be on alert if you get any unsolicited or suspicious emails claiming to be from M&S.
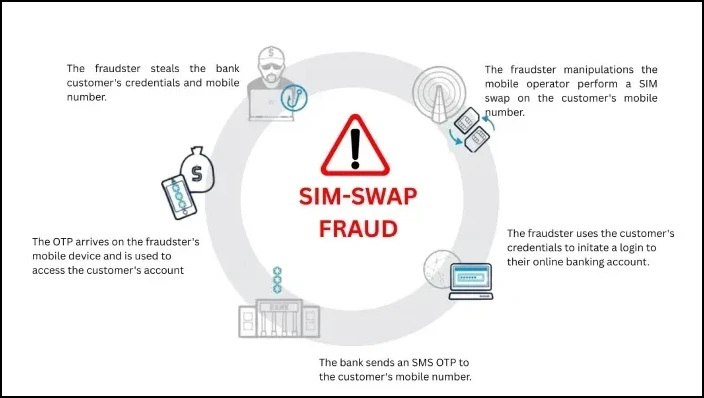
SK Telecom Alerts Customers After Malware Breach Exposes USIM Data
SK Telecom, South Korea’s largest mobile network provider, also confirmed a malware attack that exposed sensitive data linked to customers’ USIM cards. The breach was discovered late on 19 April 2025 when most teams were minimally staffed.
The malware was found on their internal systems at around 11 PM, and the breach occurred during the weekend, which is a period often targeted by attackers due to reduced staff presence. It gave unauthorized access to USIM-related data, including critical information like the International Mobile Subscriber Identity (IMSI), phone numbers (MSISDN), network authentication keys, usage history, and some stored messages and contacts.
This kind of data can potentially be exploited for SIM-swap fraud, user tracking, or even surveillance. Once the issue was detected, SK Telecom took immediate action by removing the malware and isolating affected systems. The incident was also reported to national cybersecurity authorities, and an investigation is currently ongoing but the total impact and origin of the breach have not been confirmed yet.
In the meantime, users should activate SK Telecom’s USIM protection service to block unauthorized SIM transfers. Regularly monitoring any suspicious activity or service disruption is also recommended.
User Token Logging Error Triggers Microsoft Entra Account Lockouts
Several organizations experienced sudden Microsoft Entra account lockouts over the weekend. Microsoft has now confirmed the issue was caused by an internal mistake involving user token logs.
The incident began early Saturday when many enterprises received Entra alerts suggesting leaked credentials, which triggered automatic account lockouts. At first, some administrators suspected a new enterprise app called “MACE Credential Revocation” was responsible, as it had just been installed. However, Microsoft later clarified that the problem was due to the accidental logging of short-lived user refresh tokens (actual login data) rather than just token metadata, which is the usual practice. This happened with a small group of users.
Once Microsoft noticed the issue, it acted quickly by invalidating the affected tokens to protect users. Unfortunately, this triggered Entra’s security system to flag the accounts as compromised, resulting in widespread lockouts between 4:00 AM and 9:00 AM UTC on April 20, 2025. They stressed there’s no evidence of unauthorized access and promised to conduct a full review, sharing the results with affected customers. If you want to restore access, admins can mark users as safe in Microsoft Entra. As always, keep your systems updated and monitor security alerts closely to prevent disruption. For more resolution steps, please refer to this link.