
Do Office 365 Users Need DMARC? Configuring DMARC for Office 365
If you are seeking a one-liner answer to ‘Do Office 365 users need DMARC?’ then it’s ‘Yes, they do need DMARC protection.

If you are seeking a one-liner answer to ‘Do Office 365 users need DMARC?’ then it’s ‘Yes, they do need DMARC protection.
![US Sanctions Kimsuky, Ukraine Hacks Russia, Tree Breach: 2M – Cybersecurity News [November 27, 2023]](https://www.duocircle.com/wp-content/uploads/2023/12/spf-validator.jpg)
The realm of cybersecurity is indeed dynamic, exciting, and continually evolving, and this week has been no exception. From Dollar Tree’s data breaches to the Russian Aviation hack, here’s the latest scoop on cybersecurity around the world.
![Kansas Cyberattack Investigation, Lab Data Breach, Defender Bounty Program – Cybersecurity News [November 20, 2023]](https://www.duocircle.com/wp-content/uploads/2023/11/what-is-dkim-selector.jpg)
The week was full of thrilling and chilling cybersecurity news and updates. From ransomware hitting Kansas Courts to Bloomberg Crypto phishing campaign, here’s the scoop on the latest in cybersecurity this week.

Email service providers have been constantly trying to cut off all possible ways hackers exploit to send phishing and spoofing emails. Recently, Google has made another announcement according to which any company sending more than 5,000 emails per day is required to deploy DMARC to minimize the likelihood of recipients receiving fraudulent and phish-y messages. Moreover, incorporating the one-click unsubscribing feature has also become mandatory to ensure receivers aren’t bombarded with hundreds of unwanted marketing emails.
![SEC Ransomware Complaint, Rhysida Alert Issued, Ethereum Theft Exploit – Cybersecurity News [November 13, 2023]](https://www.duocircle.com/wp-content/uploads/2023/11/DMARC-generator.jpg)
Welcome to this week’s edition of the ‘Weekly Cybersecurity Bulletin’ where we slice through the complexity of the digital security landscape to bring you the most pertinent news and updates making headlines around the world. From threat actors lodging SEC complaints to Phaas gangs getting arrested, this text has it all.
SPF, DKIM, and DMARC were introduced to the world to help verify an email sender’s authenticity and if any changes were made to the content in transit. Their adoption has been slow, partly because businesses don’t have clarity on their functions.
![Canadian Device Restrictions, US Targets Ryuk, FBI: Casinos Targeted – Cybersecurity News [November 06, 2023]](https://www.duocircle.com/wp-content/uploads/2023/11/dmarc-report-service.jpg)
The week has been full of cybersecurity news that continues to shake the cyber world as usual. Here’s our latest cybersecurity news piece sharing the latest developments to help you keep a step ahead of threat actors.

The responsibility of handling data comes with its own intricacies, but adhering to global data compliance laws makes the situation a bit sorted. By sorted, we don’t mean easy, but rather uniform. These laws are introduced to safeguard the privacy of customers and users while ensuring companies run their operations using the requisite details and documents. Moreover, adhering to these laws and best practices reflects your concern about cybersecurity, which consequently boosts your image as a responsible and trusted company.
![Apple Device Email Breach, Russian Email Breach, Microsoft Enhances Security – Cybersecurity News [October 30, 2023]](https://www.duocircle.com/wp-content/uploads/2023/11/buy-smtp-1.jpg)
Here are the latest updates related to the email security landscape, exploring the newest email security breaches and measures to combat threats that involve big names like the Pentagon and Microsoft.
A DNS record is a domain name system record that helps users visit a website without having to memorize its IP address. It basically translates easy-to-remember domain names to their corresponding IP addresses and presents the desired web results.
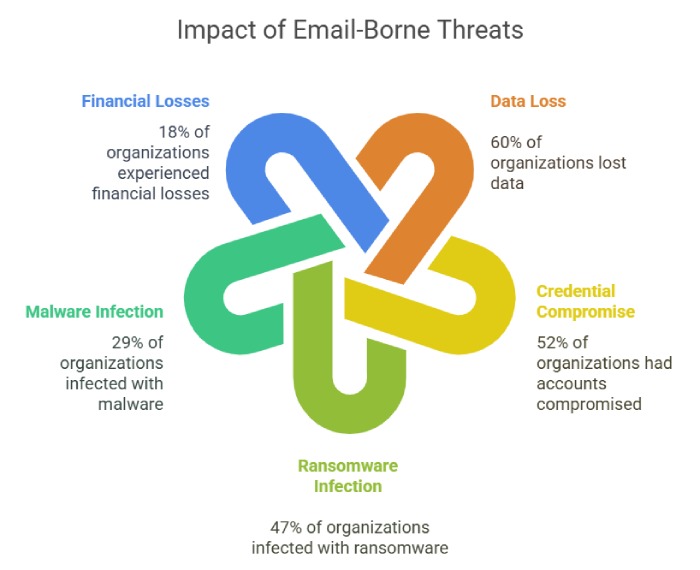
As they continue to grow in number, phishing emails have become a significant concern in the cybersecurity landscape. In October 2022, there were a staggering 101,104 unique email subjects associated with these fraudulent emails.
![ClearFake Scam Warning, Google’s DigiKavach Innovation, FBI Phantom Hacker Alert – Cybersecurity News [October 16, 2023]](https://www.duocircle.com/wp-content/uploads/2023/10/dkim-record-check-2.jpg)
Here’s your weekly dive into the cyber world! We’re here to keep you in the loop about the newest scams, FBI alerts, and all the cool new tools and initiatives in the cybersecurity realm. Let’s take a look!
In a recent study, Cornell University researchers have uncovered a startling new threat to cybersecurity: the use of AI models to steal passwords by analyzing the acoustic side-channel, or the sounds made while typing on a keyboard. This AI model achieved an alarming 95% accuracy rate in stealing passwords — the highest accuracy seen without the use of a language model, which emphasizes the need for increased vigilance in digital security.

Paying off ransom in exchange for information isn’t a new concerning tangent for the cybersecurity Ninjas. However, the UK has been recently bombarded with a series of ransomware attacks, especially steered towards the police and the education sector.
![Email Authentication Upgrade, BMC Firmware Concerns, Exim Mail Vulnerabilities – Cybersecurity News [October 02, 2023]](https://www.duocircle.com/wp-content/uploads/2023/10/what-is-dmarc.jpg)
In the ever-evolving digital landscape, cyber threats are constantly mutating and growing in sophistication. As we turn the digital pages of another week, we’re met with a slew of cyberattacks that have stirred conversations and raised eyebrows across the tech sphere. Here’s a close look at the latest email security news causing debates in the tech industry.

Cyber actors have been exploiting different online means to trick people and demand hefty ransom. They gain unauthorized access to systems and then steal, encrypt, or intercept sensitive information to blackmail reputed companies.
![Deceptive ‘Zero Font’ Scam, Chinese Cyberattack: 60,000 Emails – Cybersecurity News [September 25, 2023]](https://www.duocircle.com/wp-content/uploads/2023/10/spf-record-1.jpg)
Stay in the loop with the recent email security update, providing insights on the newest phishing threats, email breaches, and beyond.

Bumblebee malware makes a comeback with email attacks. Here’s a close look at the episode, the threat actors, and how to protect yourself from such threats.
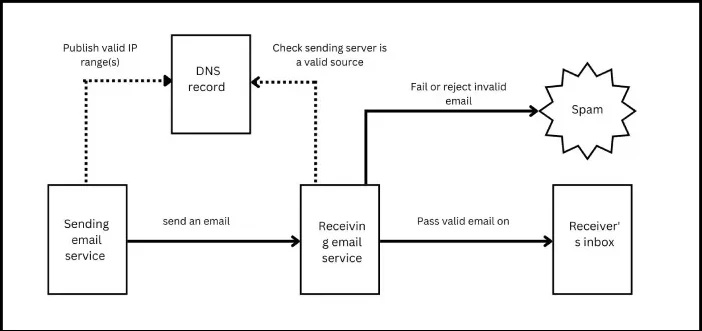
These days, every website is on the radar of malicious actors; doesn’t matter if you own a multi-national company or a home-grown e-commerce platform. You have a website, that means you have to be cautious and driven towards email authentication based on SPF, DKIM, and DMARC.
![Google Looker Evades, Email Scam Collaboration, Firefox Zero-Day Patch Cybersecurity News [September 11, 2023]](https://www.duocircle.com/wp-content/uploads/2023/09/dkim-record-check-1-1.jpg)
Cybersecurity is a rapidly evolving domain that requires you to be updated with information on the latest innovations to stay on top. To help in the process of making email security and organizational cyber well-being possible, here are the top cybersecurity headlines from this week: