The early-2025 global posture of DMARC
It’s been more than a year since Google and Yahoo pushed domain owners to adopt DMARC. This push has paid off partially— why partially? Because the number of domains with DMARC has doubled, but they aren’t configured strictly. Domain owners have just implemented DMARC for the sake of it, but have done nothing to advance the policies and strengthen email security. As per a survey done by Mailgun, 66% of senders are aware that they are using both SPF and DKIM for email authentication. About 25.7% of respondents don’t know how their organizations are using DKIM and SPF, and less than 9% said they are using only one of the two.
DMARC is an email authentication protocol that works on the basis of SPF and DKIM results. SPF allows domain owners to specify the mail servers they trust to be used for sending emails on their behalf. DKIM, on the other hand, helps recipients’ mail servers figure out if the email content was tampered with in transit. For an email to pass DMARC verification checks, it has to pass at least one of the protocols— SPF or DKIM. For emails that don’t pass SPF and/or DKIM, DMARC instructs the receiving mailboxes on how to treat them. It’s the domain owner that sets the instructions in the DMARC record. There are three options (DMARC policies) that they can choose from and set—
- p=none, which basically tells receiving servers to treat failed emails as usual.
- p=quarantine, which instructs the receiving servers to mark the failed .
- p=reject, if you set your DMARC record to this policy, then all the emails that failed the DMARC verification checks are denied entry to the recipient’s mailbox. They don’t get placed in the junk folder even; they are simply bounced back to the sender.
Now, the problem with the recent adoption is that most domain owners have set their record to p=none, which is only meant for monitoring the flow of emails. It should be used in the initial phase of deployment to understand the email structure while not disrupting the flow of emails in any way. However, domain owners do not care about advancing the policy to stricter options— p=quarantine or p=reject. Only 37% of the surveyed senders who use DMARC know they are enforcing it with either p=quarantine or p=reject.
We understand this problem arises primarily because of the lack of awareness. Domain owners just did enough to stay compliant with Google and Yahoo’s new requirements. This underlines the need for industry experts and tech biggies to come together and propagate the importance of strategically advancing DMARC policies. Without p=quarantine or p=reject, your domain is as vulnerable to phishing as it was before you had DMARC on for it. It makes no change.
The near future of DMARC adoption
It’s not just Google, Yahoo, and Outlook that are contributing to the pace of DMARC adoption. The recent Payment Card Industry Data Security Standard, or PCI DSS version 4.0, also requires DMARC for all organizations storing credit card details. The European Union’s Digital Operational Resilience Act, or DORA, has also mandated DMARC for its ability to report on and block impersonation.
With such regulations and legislations being the tipping point, organizations have also quickened the adoption process so as to stay safe from legal and compliance penalties. After all, nobody wants to meet with hefty regulatory actions and the possibility of class action lawsuits.
Lookalike domains are on the rise
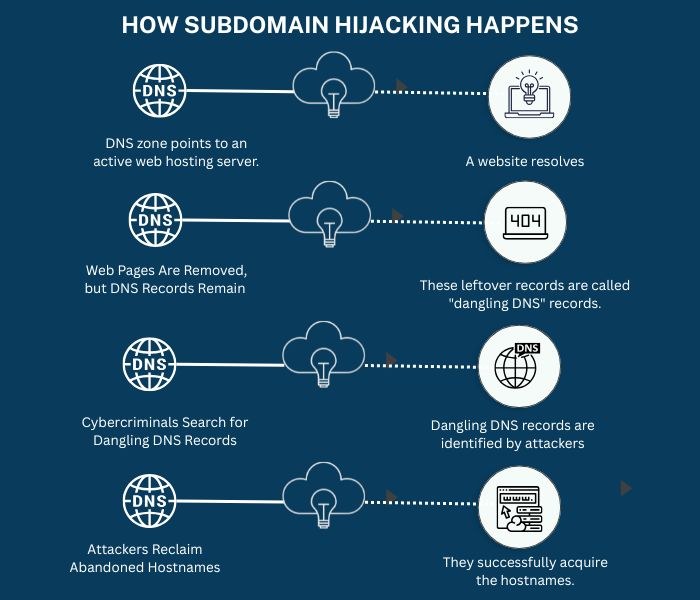
Now that most domains have DMARC linked with them, threat actors are buying lookalike domains to send illegitimate emails on behalf of credible brands. One method attackers use to bypass DMARC is known as “subdomain spoofing.” In this technique, they look for SPF records that reference domains that are no longer registered. By taking control of these abandoned (or orphaned) domains, attackers can exploit the inherited SPF permissions to launch large-scale spam or phishing campaigns.
Improper DKIM key rotation is putting email security at risk
DKIM works by using two cryptographic keys— a private one and a public one. Together, these keys help verify the integrity of the email and that the content wasn’t tampered with in transit. The private key adds a digital signature to outgoing emails, while the public key is stored in your DNS. Email providers use the public key to check if the message is genuine.
To stay secure, DKIM keys should be changed regularly—a process called DKIM key rotation. It’s like updating your passwords to prevent hackers from getting in.
Unfortunately, most senders aren’t doing this enough. Nearly half (47.7%) only rotate keys after a security problem, and 40% aren’t even sure how often they should do it. That means only about 12% have a clear schedule, leaving everyone else—and their customers—at risk.
If someone gets hold of your DKIM keys, they can send emails that look exactly like they’re from your domain—no spoofing tricks needed.
BIMI is next in line for strengthening email security
DMARC has an amazing reporting feature that gives domain owners insights into email activities. By carefully evaluating DMARC reports, you know if there are any misconfigurations that require your immediate attention and if an unauthorized entity is sending emails on your behalf. This really helps in moving from p=none to p=quarantine or p=reject.
In addition to leveraging the benefits of DMARC reporting, companies also need to take the next step— moving to Brand Indicators for Message Identification or BIMI. This email security protocol allows companies to affix their logo next to their emails. But to do this, you need to ensure your DMARC is configured properly and is set to strict policies.
DuoCircle is at your rescue!
The gist of the story is that you must use DMARC’s reporting feature, which allows you to take result-driven action regarding policy adjustments and fixing other misconfigurations. We understand that evaluating these reports is easier said than done, so we offer the service of assessing the DMARC aggregate and forensic reports and suggesting the appropriate changes. Contact us today to learn more about it.