What are the most important email security protocols, and how do they protect your communications?
If you send marketing email campaigns to your clients almost every day, you will know that email is one of the key channels to connect with your audience. But what you might not realize is that it is also the most vulnerable channel that lets cybercriminals in and leaves your entire ecosystem exposed to phishing, spoofing attacks, and data breaches.
If you think this happens to only one in a million businesses and you could never be one of those targets, you’re wrong!
Cybercriminals spare no one, and worse still, no opportunity!
So, does this mean you can never make the best of this mode of communication? Not necessarily! You can absolutely leverage the power of emails while protecting your organization from grave email-based cyberattacks by deploying email security protocols.
These protocols are more than just technical solutions that ward off cyber attackers; they are safeguards that authenticate your sending domains, encrypt messages, and ensure that only legitimate communications reach your recipients.
In this article, we’ll dig into these authentication protocols that should definitely be a part of your email security framework.
What are the common email security protocols that protect your emails?
Speaking of security protocols for your email setup, there are a wide range of them out there, each of which is designed to address a unique aspect of email security, ranging from encryption to sender authentication and spam prevention.
So, which of these security protocols is the right fit for you? Should you rely on a single security protocol or use them together for a more comprehensive security approach? Here, we will talk about the major email security standards, how they have evolved over time, and how you can leverage them to strengthen security and reduce the risk of phishing, spoofing, and unauthorized access.
SSL/TLS for HTTPS
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are cryptographic protocols that encrypt data in transit to provide secure communication between email clients, web browsers, and servers.
SSL first appeared on the scene in 1995 as the first widely adopted protocol for secure online communication, but it had its flaws.
To fill the gaps and security vulnerabilities left by SSL, TLS was introduced as its successor in 1999, which offered enhanced security with authentication, data integrity, and confidentiality.
Remember the “S” in HTTPS? That is for “Secure,” meaning a website or online service is utilizing SSL/TLS to establish an encrypted connection.
SMTPS
SMTPS (SMTP Secure) protects your emails in transit from one server to another. When Simple Mail Transfer Protocol (SMTP) was first created, it was not secure, and hackers could intercept emails and read or modify them. SMTPS fixes this by encrypting the connection between email servers so that no one can intercept your emails in transit.
SMTPS does this by using TLS (Transport Layer Security) to encode (encrypt) emails as encrypted text before sending them. That way, even if someone tries to steal the email, they can’t read it. SMTPS only protects emails during sending, however, and not after they are in the inbox.
StartTLS
StartTLS is not really an email protocol; it is an email protocol command that tells the email server to convert an unencrypted connection into an encrypted connection using SSL or TLS. Although it is an extension of SMTP, it slightly differs from it. Unlike SMTP, which uses a specific port for encryption, StartTLS uses normal email ports— port 587 for sending mail and port 25 for server-to-server mail.
When you send an email, your email client first opens a connection to the server in unencrypted form. It then sends a StartTLS command asking the server to switch to a secure, encrypted connection. If the server supports TLS, the connection is encrypted, protecting your email from being intercepted during transmission.
There are some disadvantages of StartTLS, though. It protects emails only during transit and doesn’t protect them once they’ve reached the mailbox of the recipient. Also, if an email server does not support encryption or is malicious, the StartTLS command might still allow the connection, but without encryption—your email would be sent in plain text, vulnerable to hackers.
SMTP MTA-STS
SMTP MTA-STS (Mail Transfer Agent Strict Transport Security) is an email security protocol that guarantees that emails are always transmitted over an encrypted connection. It does so through the capacity of email servers to set rules (MTA-STS policy) that require that all emails must be transmitted with TLS encryption when delivered. When an email is to be sent, the sender’s mail server first checks whether the receiving server has an MTA-STS policy.
If it does, the email will only be transmitted over a secure TLS connection. If a secure connection cannot be established, the email will not be sent at all so that it cannot be transmitted over an insecure network, where attackers can intercept or modify the message. This prevents attacks like man-in-the-middle attacks and makes emails in transit safe.
Perhaps one of the biggest advantages of this protocol is that it stops attackers from forcing mail servers to send emails without encryption, which is done in some types of cyberattacks.
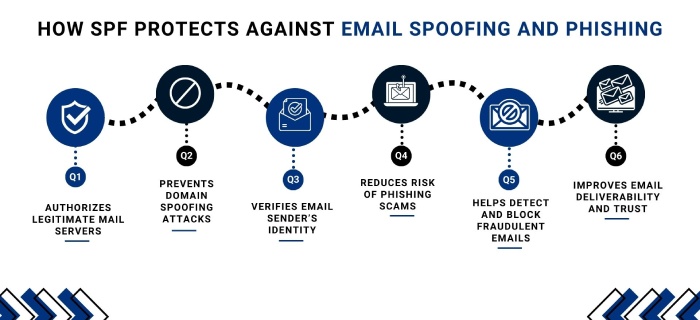
SPF
SPF (Sender Policy Framework) is a security standard that stops your email domain from being used by spammers. SPF lets you specify which mail servers are authorized to send mail on your behalf. Without SPF, anyone can send mail using your domain name, and that is how phishing scams make people think fake emails are real. When an email is sent to the recipient, their mail server checks your SPF record to see if the email really came from an authorized server. If it did, then the email is considered legitimate. If not, the email might get marked as spam, marked suspicious, or rejected to stop fraud.
To implement SPF, you need to add an SPF record in the DNS settings of your domain. The record is just a list of servers and IP addresses that can send mail to your domain.
DKIM
DKIM (DomainKeys Identified Mail) is a security feature that helps make sure that your outgoing emails are not changed or messed with while they are being sent. When an email is sent, the sending mail server attaches a unique digital signature to it. This signature is created using a private cryptographic key, and a matching public key is stored in the DNS settings of the your email-sending domain. When the email reaches the receiver, their mail server checks the signature using the public key. If the signature matches, it means the email was not altered during transit, so the email is safe. If the signature doesn’t match or is missing, the email might be marked as spam or suspicious.
DKIM works in the background, so those sending or receiving emails don’t see these signatures—it all happens at the server level. While DKIM is great for making sure emails aren’t changed, it doesn’t check who sent them. That’s why it should be used along with SPF and DMARC.
DMARC
This brings us to the next security protocol that ties it all together— DMARC. Domain-based Message Authentication, Reporting, and Conformance is a security feature that works together with SPF and DKIM to stop fake emails and protect your domain from phishing attacks.
SPF checks whether an email has been sent from an authorized mail server, and DKIM verifies that the email has not been tampered with on its way. But without DMARC, even if an email fails these authentication checks, it gets delivered—allowing spammers to still use your domain to send spam messages. DMARC solves this issue by providing instructions on what to do with failing SPF or DKIM.
To set up DMARC, you need to add a DMARC record in your domain’s DNS setup. This record instructs receiving mail servers to reject, mark as spam, or simply pass emails that have failed the security checks. DMARC also provides reports so you can identify if someone is attempting to send spam emails from your domain.
Digital certificates
Using digital certificates is another way you can protect your organization from falling prey to phishing scams and other email-based attacks. These certificates are like online ID cards that verify the identity of the email sender and ensure that the message is authentic and untampered.
Basically, these certificates use public key cryptography, where you (the sender) encrypt the outgoing message using a private key. The recipient then uses a public key associated with your certificate to decrypt and verify the message. Doing this ensures that the message is received and read by only those who are meant to receive it and has not been tampered with by a cyber criminal along the way.
Which security protocol is best for your organization?
There’s no one-size-fits-all approach when it comes to email security, but there are certain protocols that you should definitely include in your cybersecurity setup. For starters, DMARC is one such protocol that protects your organization against phishing and spoofing while ensuring that your emails reach their destination without a hitch.
To get started with DMARC implementation or DMARC reporting, get in touch with us today!