What is IoT email authentication, and why should you care about it?
If you look around and notice the gadgets you use every day and how interconnected they are, you will realize that these gadgets are constantly communicating with each other and with users over the internet. Whether it is your smartwatch and your phone or the security camera in your home and the cloud storage service, almost everything that you use is part of the ecosystem that is called IoT or Internet of Things.
This interconnectedness offered by IoT is certainly a game-changer as it offers convenience, automation, and efficiency. But that’s not all! This interconnectedness is more like a double-edged sword—on one hand, it makes life significantly easier, but on the other hand, it exposes you to serious cybersecurity threats.
The thing about IoT (like almost any other technology) is that you can certainly leverage it to enhance productivity, security, and efficiency, but that does not mean you are oblivious to the risks it entails or brings along. Often, we are so carried away by the convenience and innovation that IoT offers that we fail to look at its security aspect. An important aspect of security here is email authentication.
In this article, we will take a look at what exactly email authentication is and why it is so important in today’s digital landscape.
What does email have to do with IoT?
Email has now become the most preferred communication channel, and rightly so. It is used across industries by different stakeholders to send alerts, updates, and important notifications. Now that it has become such an integral aspect of our lives, it has made its way into the IoT ecosystem as well.
IoT devices, whether they are smart home gadgets, industrial sensors, or healthcare monitors, often rely on emails to keep users and organizations informed. When we talk of IoT, we’re not just referring to consumer devices but also industrial systems, transportation networks, healthcare equipment, etc.
These devices send out automatic emails for various reasons, like regular notifications, status updates, reminders for maintenance, and reports to keep the businesses and users informed.
For example, an industrial sensor can send an email when a machine is overheating, a medical device can alert doctors about the status of a patient, or a transport system can send reports on vehicle performance. Manufacturers also email firmware updates, repair instructions, and support messages to make devices work properly.
Since so much critical information is transmitted by email, security becomes an important concern. If email communication is not secured, hackers can spoof emails claiming to be from an IoT device. That will result in phishing attacks, stolen data, or even unauthorized access to the system. This is where email authentication comes into play —it protects emails sent by IoT devices from being forged and manipulated by attackers.
What are the common email security risks in the IoT ecosystem?
Email is an important communication channel not just for you and your business but also for cyberattackers, especially when there are gaps in security measures. With so many devices connected to each other in an IoT ecosystem, gaps in security and vulnerabilities are bound to occur. The sooner you identify these gaps and patch them, the lower the risk of cyber attackers infiltrating your system.
As you already know, IoT devices send alerts, updates, and notifications via email; the problem arises when cybercriminals use them as an opportunity to launch their malicious attacks.
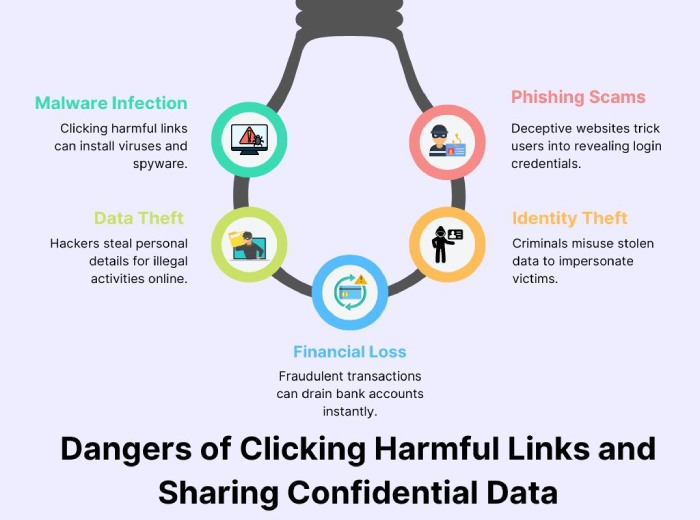
One of the most common ways in which these attacks gain control over your devices and, subsequently, your system is through phishing emails. Here, the attacker sends spoof emails that seem to come from a trusted device or service. These emails often contain harmful links or attachments. If a user clicks on them, the attacker can steal personal data, install malware, or even take control of the device.
Another major security risk that IoT systems are vulnerable to is Man-in-the-Middle attacks. In this attack, a threat actor intercepts email communication between a user and an IoT device. They can modify the message content, steal credentials, or misdirect users to spoofed websites.
Email spoofing is also a serious threat. Cyber attackers send emails from forged sender addresses to make them appear genuine. Without effective email verification protocols such as SPF, DKIM, and DMARC, it’s hard to confirm whether an email is genuine or suspicious.
What are the common IoT and email security challenges?
Let’s face it: the interconnectedness is not entirely about convenience but also about security risks that creep in. Since IoT devices use emails to send notifications, updates, and alerts, cyberattackers find it easy to capitalize on vulnerabilities.
Here are some of the most common IoT and email security challenges:
Fake emails and phishing attacks
Hackers often send fraudulent emails that look real. They make these messages look like they’re coming from your IoT device or service provider and request that you click on a link or download a file. If you click on it, the attacker gets your login information, installs malware, or even takes over your device. The issue is that most users don’t have any idea how to identify these fraudulent emails, which leads them into bigger problems like identity theft, financial loss, or complete device compromise.
Gaps in email authentication
Most businesses think that once they set up an IoT device or system, their job is done. But that’s not how it works. To ensure that emails from IoT devices are genuine and are not spoofed by attackers, you must have proper authentication mechanisms in place. But the thing is, many organizations neglect email authentication and fail to implement security measures such as SPF, DKIM, and DMARC. Without these security measures, hackers can use phishing emails that mimic legitimate IoT devices, and the users end up clicking on harmful links or giving out confidential data.
Lack of email encryption
There are IoT devices that send sensitive data through email without encryption. What this means is that if an email is hacked by a hacker, they will be able to read, steal, or manipulate the data. This exposes personal information, security logs, and system notifications. This happens because of a lack of strong encryption, which prevents the hackers from intercepting email communication.
Unsafe firmware and security updates
Most IoT devices get important software updates through email alerts. Hackers can intercept or even send spoofed update emails with malware if these emails are not secured. When a user installs a spoofed update, their device may be taken over, hacked, or even used in a bigger cyberattack.
How does DMARC help secure IoT email communication?
One thing’s clear: you have to deploy proper security measures when dealing with IoT email communication. With all these IoT devices sending notifications, updates, and alerts, hackers find a huge opportunity to spoof emails, launch phishing attacks, and trick users into divulging sensitive information. That is where DMARC (Domain-based Message Authentication, Reporting, and Conformance) enters the picture. It ensures that emails from IoT devices are legitimate, authenticated, and safe from attackers.
Here’s how it helps:
Stops fake emails from IoT devices
DMARC enhances the security of emails sent from IoT devices so that only legitimate messages reach the recipients. It blocks email spoofing and limits the possibility of phishing attacks. If you do not have DMARC in place, your clients would never know if the email is coming from a legitimate source (in this case, the IoT device they’re using) or if it is yet another malicious tactic of an attacker.
Enhance trust and brand integrity
Your brand is nothing without your customers’ trust, and to gain their trust, you must show them that you prioritize security and protect their data. If the customers realize that they’re receiving spoofed emails on your behalf, they might not be able to trust the ones that are actually coming from you. This damages your reputation and can lead to the loss of customer confidence. But with DMARC in place, you and your customers can rest assured that all the email communication from your brand is legitimate and authenticated, which means that their data is well-protected.
Easier integration with enterprise systems
For IoT devices running on enterprise systems, DMARC is not just a security feature; it is essential. For enterprise systems, you require secure and seamless communication within the network, and this is only possible if you have implemented DMARC. With your outgoing emails authenticated by DMARC, email servers can be assured that emails from your IoT devices are authentic and secure. This makes sure that critical reminders, notices, and alerts are not rejected, blocked, or marked as spam by security filters and that they reach their destination— the recipient’s inbox.
Now that you already know that DMARC is the ultimate solution for most of your email security woes, implementing it is no longer an option—it’s a necessity.
So, if your business relies on IoT systems or manages them, take this as a sign to deploy DMARC right away! To get started, contact us today!